In 2020, many organizations pivoted their business models due to the global pandemic. If you're one of these companies, you may have developed new processes and procedures that allowed you to safely continue operations and maintain high levels of customer service. Now, the effects of the pandemic have changed the face of how business gets done and potentially introduced new cybersecurity risks. In this article, we offer practical guidance on how to classify and measure these risks for effective cybersecurity risk management.
Understanding Modern Technology Risks
 Before the days of the cloud (pre-2008), technology risks were generally associated with a physical facility disaster like a fire, flood, or nor'easter. Since everything lived within the company's four walls (servers, files, applications, etc.), an event like a building fire could mean absolute devastation. To mitigate that risk, appropriate controls were put in place for the situation, such as off-site backup tapes (air-gap solution) and disaster recovery centers.
Before the days of the cloud (pre-2008), technology risks were generally associated with a physical facility disaster like a fire, flood, or nor'easter. Since everything lived within the company's four walls (servers, files, applications, etc.), an event like a building fire could mean absolute devastation. To mitigate that risk, appropriate controls were put in place for the situation, such as off-site backup tapes (air-gap solution) and disaster recovery centers.
Fast forward to the post-pandemic cloud era; risks and disasters today look very different for organizations. These highly disruptive events come in many different forms, including ransomware attacks, social engineering, phishing attacks, and major internet outages. On top of that, we're seeing state-sponsored threat actors expanding their reach by actively attacking small- to medium-sized businesses as well as large corporations. These disasters look different, and the likelihood of one occurring is much higher than ever. In many cases, these risks could have been avoided or mitigated with proper planning. Below is a high-level look into how your organization can begin approaching and measuring your cybersecurity risks.
How to Approach Risk Management
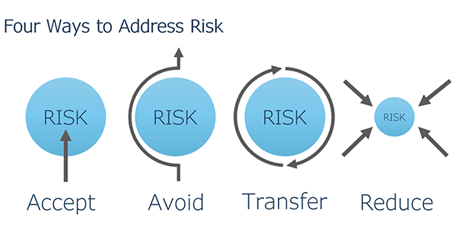
It's important to have a thorough understanding of organizational risk and the potential impact it can have on your business. At a high level, there are four ways you can approach risk to classify and address each threat.
1. ACCEPT | Do nothing.
Decide it is a tolerable risk, but make sure it's a fully informed decision.
2. AVOID | Eliminate risk.
For example, don’t allow remote access to your network if the risk is too high. You can also consider not getting into a particular line of business entirely, i.e., deciding not to take on hospitals as customers because HIPAA regulations are too costly and the risk of non-compliance is too high. Risk avoidance is typically the most expensive path.
3. TRANSFER | Give risk to a willing 3rd party.
Transfer risk to another 3rd party (Payroll service, Cyber/E&O/GL Insurance) that only protects a specific data type. Be aware that you're not transferring all of your responsibility. It should be part of your due diligence to ensure the third-party provider is doing its part to properly secure and backup data in the event of a failure or breach.
4. REDUCE | Put technology controls in place.
This is where Systems Engineering prefers to focus. We find ways to help businesses enable their employees to work in the most efficient and secure manner possible. To accomplish this, organizations need to blend the right mix of technologies, policies, and training that reduce associated risks to an acceptable level.
How to Measure Your Cybersecurity Risks
Once you've classified your risks, it is time to take inventory of all the cybersecurity or disaster events you can think of, and rank them against business priorities. You can walk through a simple in-house whiteboarding exercise to visualize your “Acceptable Risk”. Here is a sample chart outline of what this type of exercise might look like in a typical organization.
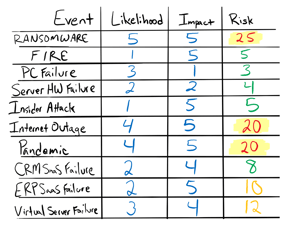
1. Take inventory of all risks.
Write down every event that could threaten your business in column one.
2. Score your risks.
Give the risks you've identified a score. In this example, we used a scoring scale of 1 to 5, with 5 being the most impactful. Score the likelihood of the event happening along with the perceived impact the event would have on your business.
2. Calculate your overall risks.
Once each risk is listed out and scored, a simple formula can be applied to calculate the overall risk:
Calculate Acceptable Risk:
Likelihood x Impact = Risk
This type of scoring system gives you a way to measure cybersecurity risks, identify what is acceptable and what needs addressing, and give priority to reducing them. Using an exercise like the above is an essential step in determining acceptable risk levels within your company for each identified event.
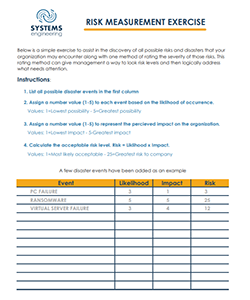 |
|
Click Template to Download PDF |
Risks are always evolving, so doing an acceptable risk exercise should not be a one-time event. There may be risks that were not initially considered, or a major company procedure may have changed since your last session (moving files from an on-premises server to the cloud). If you would like to try this exercise to assess your own company risks, we created a downloadable Acceptable Risk chart to use as a guide in your own whiteboarding session.
If you have any questions on the process for identifying and scoring your cybersecurity risks, please reach out to your Systems Engineering Account Manager, or email us at info@systemsengineering.com.
After you have identified and scored your cybersecurity risks, the logical next step is to address them. Take a look at the framework we use to help organizations address and reduce their cybersecurity risks and vulnerabilities.

 Brad Sprague is the leader of Systems Engineering's Account Managers. Since 2003, he has worked closely with clients to develop strategic technology roadmaps, cybersecurity strategies, multi-year budgets, and IT support plans.
Brad Sprague is the leader of Systems Engineering's Account Managers. Since 2003, he has worked closely with clients to develop strategic technology roadmaps, cybersecurity strategies, multi-year budgets, and IT support plans.