Since 2008, Verizon has released its annual Data Breach Investigations Report (DBIR). This is a data-driven report on threats your organization may encounter in regard to cybercrime. The threats identified are the most common tactics used against organizations that resulted in a data breach. We use this annual source of authority for timely insights that can protect your company and its assets. This year, the DBIR analyzed 23,896 security incidents, of which 5,212, or 22%, were confirmed data breaches.

Below are the five critical questions you might have about a data breach:
How are they getting In?
The DBIR identifies four critical paths leading into your network. Credential compromise (username and passwords) and successful phishing attacks represent a sizeable majority of compromised cases. For Systems Engineering, this leads us to two conclusions. First, the prevalence of successful attacks targeting an organization at the end-user level is at an all-time high. Second, deploying multi-factor authentication (MFA) and ensuring that your employee base receives high-quality and instructive end-user security awareness training provides the highest value security solutions to protect your organization against credential compromise and phishing attacks.
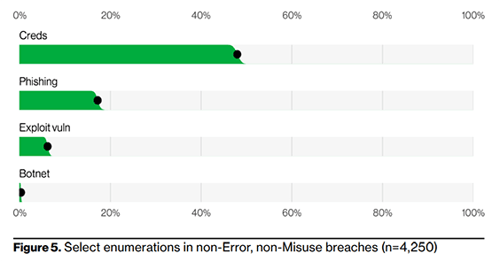
How are vulnerabilities addressed?
As we can see above, Exploited Vulnerabilities and BotNet Intrusions represent relatively small portions of successful data breaches as common practices of managed patching and universal threat management (UTM) firewalls have developed to address these attack vectors. Certain types of attacks have become less common as standard security tools are baked into all applicable solutions.
With that said, the human element of cybersecurity remains the most prevalent (involved in 82% of breach activity) and the most difficult to control unless your organization invests in the tools and tasks required to develop a strong, internal culture of security.
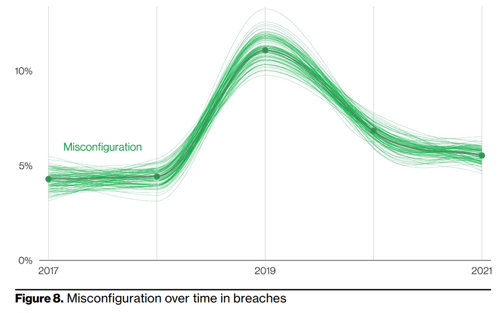
In Figure 8, Verizon represents another element of human error as the culprit of a compromise—simple misconfiguration, meaning a firewall port left open during a new deployment, or similar examples where an attack vector was left unsecured during manual device configurations. The spike in 2019 represents compromises due to misconfigured devices. Where a prevalence of successful attacks becomes apparent, the cybersecurity industry typically and quickly tends to invest capital in the development of a technology solution which, in this example, would be continuous configuration management and internal vulnerability scanning assessments.
What are they after?
 We’ve looked at how breaches get started and what we can do to prevent the most common attack vectors, so now let’s understand what these attacks are targeting and the means at our disposal to protect those assets.
We’ve looked at how breaches get started and what we can do to prevent the most common attack vectors, so now let’s understand what these attacks are targeting and the means at our disposal to protect those assets.
As summarized in the DBIR, 80% of successful breaches are still carried out by persons or threat actors who are external to the organization. Additionally, these breaches are targeting your organization’s network north of 85% of the time. In the business model of cybercrime, data is the most profitable asset to steal and the easiest asset to sell. Data is also the most common asset held for ransom.
The accessibility of your server instances are primarily dictated by two things. First, the quality of your security technologies and their management. Second, by the permissions assigned on an individual user basis. A user account with poorly maintained access controls can allow for ransomware to propagate aggressively.
Once compromised, it is critically important that your organization be entirely sure that your backup data is intact. In addition, your IT team must know exactly how to restore those backups, in which order, and to which systems.
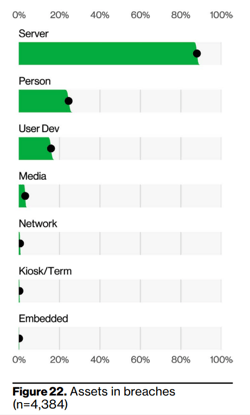
The Verizon DBIR report is intended to help you ascertain where to invest in protective technologies most effectively. The data demonstrates which type of resources and activities are most prone to be the root cause of an incident. Referencing Figure 22, your protective securities investment approach should, to some extent, be informed by the percentages expressed next to each resource category.
What's the financial impact?
The duration of a breach directly affects the number of records compromised and, hence, the financial impact of the breach on the organization. As of 2021, the average cost per breached record was found to be $161. Figure 29 below portrays that, on average, security incidents are being discovered more quickly than in years past, however, an effective ransomware attack can propagate quickly enough to do real damage in the first 24-36 hours post-compromise.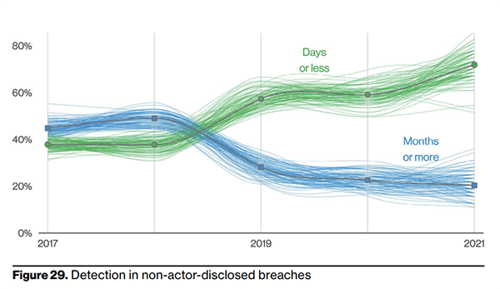
A security incident detection solution ingests all event log activity across your network and establishes a baseline for what normal network activity looks like. The tool then assesses future activity against that baseline to detect anomalous activities which could indicate a security incident.
Investing in tools that can analyze an immense volume of events per second is one of the single most valuable decisions any organization can make to ensure that, if a security incident occurs, it results in either minimal or zero records exfiltrating the network. The costs incurred from a successful compromise are quite significant due to downtime, lost business, and the potential costs to replace network infrastructure. The costs of investing in state-of-the-art prevention solutions, in comparison to the final budget of a successful data breach, make this one of the most valuable investments your organization can make.
Where are we headed?
A valuable takeaway from the DBIR is its ability to express trending activities and infer what the future may bring as a result. As we have seen, it is clear that endpoints and end-users are the targets and likely the intended victims leading into the future.
As shown below, System Intrusion, the malicious code successfully deployed within a network through compromised endpoints and end-users, is an attack vector that has skyrocketed during the advent of the cloud, the arrival of the pandemic, and the new normal of hybrid work.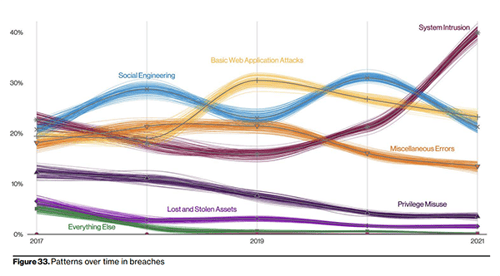 As a result, the security awareness of your employee base is incredibly important to keep your organization out of harm's way. Investing in security education is fundamental to a comprehensive security strategy. Technology solutions can all do their part, but none of them can prevent a seemingly innocent link from being clicked or a simple set of credentials from being hacked. Your people need to understand that they are the target, and responsible safety habits should be embedded in everything they do.
As a result, the security awareness of your employee base is incredibly important to keep your organization out of harm's way. Investing in security education is fundamental to a comprehensive security strategy. Technology solutions can all do their part, but none of them can prevent a seemingly innocent link from being clicked or a simple set of credentials from being hacked. Your people need to understand that they are the target, and responsible safety habits should be embedded in everything they do.
Effectively understanding where the security landscape has been and where it stands today allows organizations to make educated investments in continuous research and development of security solutions to address the threats on the horizon. A balance needs to be struck between remaining productive while maintaining your security posture across applications, devices, and the evolving needs of a hybrid work world.
Are you concerned about the current state of your organizational defenses? If you're ready to examine the security of your critical assets and discover where to make improvements in your defenses, reach out to us for more information today!
Connect with us at info@systemsengineering.com or call 888.624.6737. Customers, please get in touch with your Systems Engineering Account Manager.






