Systems Engineering is aware of two vulnerabilities, the Fortinet FortiClient EMS Pervasive SQL injection in DAS component (CVE-2023-48788) and FortiClient EMS - CSV injection in the log download feature (CVE-2023-47534).
Fortinet rates this vulnerability as CRITICAL.
Description
Fortinet has announced two vulnerabilities, one in the SQL Database portion of FortiClient EMS that could allow an unauthenticated, remote attacker to execute arbitrary code or commands (CVE-2023-48788). A successful attack would allow a malicious attacker to run administrative commands on the FortiClient EMS, compromising the device's integrity, and the devices it manages.
The other vulnerability is in relation to the CSV Log Download portion of FortiClient EMS, which could allow an unauthenticated, remote attacker to execute arbitrary code or commands (CVE-2023-47534). A successful attack would allow a malicious attacker to run administrative commands on the FortiClient EMS, compromising the device's integrity, and the devices it manages.
Please note that this is potentially being exploited in the wild, according to Fortinet.
Scope
This vulnerability is specific to Fortinet FortiClient EMS. From the Fortinet Product Security Incident Response Team (PSIRT) Advisory webpage, the following systems are affected:
CVE-2023-48788: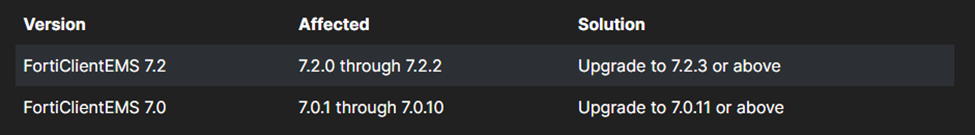
CVE-2023-47534: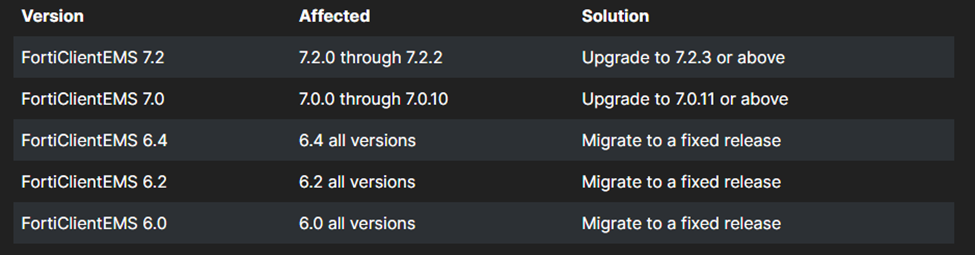
Course of Action
Fortinet has released a patch to remediate affected systems.
Given the critical nature of these vulnerabilities, Systems Engineering is proactively addressing the issue by applying patches for all clients affected by the FortiClient EMS vulnerability, regardless of service type. Our team is actively engaging with clients to provide detailed information on the timeline for remediation efforts.
If you're unsure whether these vulnerabilities impact you or need help with patching, please don't hesitate to reach out to Systems Engineering Customer Service at 207.772.4199. Our team is ready to assist you in safeguarding your system against potential threats.
If you are a Systems Engineering client and have any inquiries regarding this Security Alert, we encourage you to reach out to your dedicated Account Manager for further assistance.





