Systems Engineering is aware of two Critical Vulnerabilities, the Fortinet FortiOS - Out-of-bound Write in sslvpnd (CVE-2024-21762) and FortiOS - Format String Bug in fgfmd (CVE-2024-23113).
Fortinet rates this vulnerability as CRITICAL.
Description
Fortinet has announced two vulnerabilities, one in the SSLVPNd system that could allow an unauthenticated, remote attacker to execute arbitrary code or commands via crafted HTTP or HTTPS requests. The second vulnerability uses the fgfmd (Fortimanager connector) system that could allow an unauthenticated, remote attacker to execute arbitrary code or commands. A successful attack would allow a malicious attacker to run administrative commands on the FortiGate, compromising the device's integrity.
Please Note that this is potentially being exploited in the wild, according to Fortinet.
Scope
This vulnerability is specific to FortiGate FortiOS. From the Fortinet Product Security Incident Response Team (PSIRT) Advisory webpage, the following systems are affected:
CVE-2024-21762: 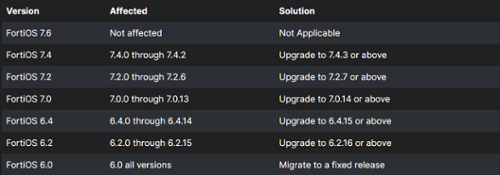
CVE-2024-23113: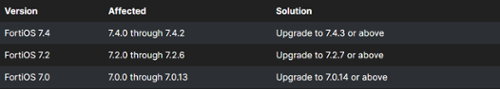
Course of Action
Fortinet has released a patch to remediate affected systems.
For clients with SE Platform, SE EventWatch, and SE Secure services, we will be proactively patching for this vulnerability and will be in contact with you with details about remediation scheduling.
For all other clients, we recommend you have your affected systems patched for this vulnerability. If you would like our assistance with patching, please reach out to Systems Engineering Customer Service at 207.772.4199 to have a ticket opened to get your system updated.
If you are a Systems Engineering client and have questions about this Security Alert, please contact your Account Manager.





