When it comes to cloud security, ensuring your sensitive data remains secure is a bigger challenge than ever. Cyberattacks are on the rise, and according to "The State of Ransomware 2020" report, businesses are attacked by cybercriminals every 11 seconds. The cost of these increasing attacks is anticipated to be around $20 billion by 2021. So how can your small to medium-sized business (SMB) protect against these organized cyberattacks? Below we review data loss prevention (DLP), which is part of a multi-layer security strategy. DLP is designed to stop the accidental (or intentional) loss of sensitive information from an organization's network, before it's too late.
All businesses have sensitive information that must be protected. This is because of its value to the cybercriminals and compliance with industry regulations and business standards like HIPAA, SOX, PCI, etc. The types of sensitive information you want to protect can include financial data, personally identifiable information (PII) like social security and credit card numbers, and intellectual property.
With the distributed nature of today's workforce, it can be easy for your data to end up in the wrong hands. Employees and remote workers have a need to communicate through cloud services like instant messaging, website forms, and file-sharing services. These are all points of egress that can allow data to leak into the wild if no policies are set. Also, it is common for confidential information to unintentionally be mishandled. A busy employee could send off an email containing PII to the wrong recipient, or they could share a social security number in a chat application for the sake of convenience. This is where a multi-layer security strategy that includes DLP becomes critical to identifying, monitoring, and automatically protecting sensitive information across your network.
What is DLP?
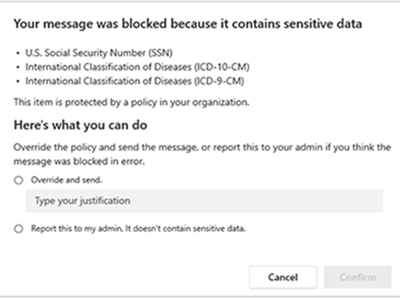
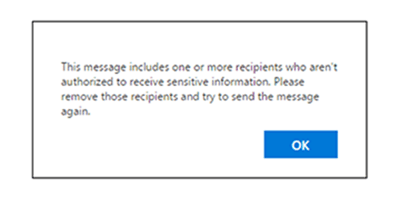
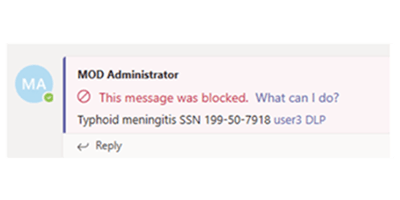
DLP describes software products and practices that help a network administrator control the transfer of data. With DLP you can make sure sensitive or critical information doesn't leave your corporate network, even by accident. A unique policy management system is used to classify and protect confidential information to keep it out of the wrong hands. For example, with DLP policies in place, if an employee accidentally (or intentionally) tried to forward a business email or chat message containing sensitive information to an unauthorized party, the employee would be denied permission. DLP can be configured to send the employee a policy tip/email notification, then document the incident within a security & compliance center report for your network administrator to review.
How DLP is used?
As part of a larger cloud security strategy, DLP will identify, monitor, and protect sensitive information across your network. Here is a practical look at how DLP is used to protect your organization's sensitive information:
Identify sensitive information across many network locations -
It is important to know where your confidential data is living within your network. You can use DLP to identify any document containing credit card numbers (or other classified and tagged data) that's stored within chosen locations.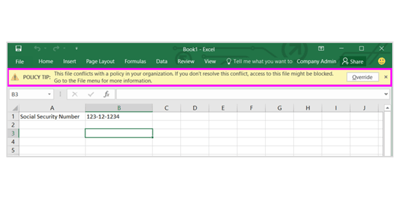
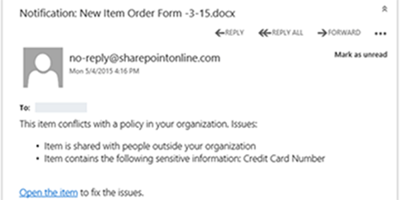
Prevent the accidental sharing of sensitive information -
Identify any document or email where PII is shared with people outside your organization, and automatically block access to that document or block the email from being sent.
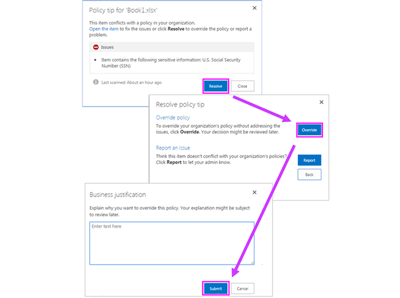
Inform employees how to stay compliant while staying productive -
When an employee attempts to send a document containing sensitive information, your DLP policy can be configured send an email notification that allows them to override the policy if they have a business justification.
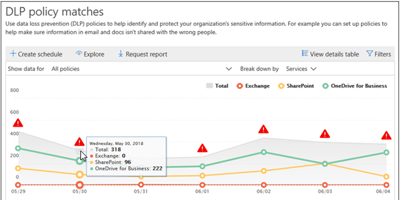
View data usage reports showing content that matches your organization's DLP policies –
After classifying and tagging data, you can see how many matches each policy and rule has over time. If your DLP policy is configured to override a policy, you can also view what users have reported.
What is important to understand is that DLP is your network watchdog, keeping an eye out for unauthorized use and transmission of critical information. There is a growing number of threats to your data, both malicious (internal or external) and accidental, so the need to consistently monitor behavior and detect risks is greater than ever. Using DLP, you gain the visibility and control needed to ensure that sensitive data is correctly used and kept out of the wrong hands.
If you would like to learn more about data loss prevention as part of a greater cloud security strategy. fill out the form below to speak with one of our cloud security experts.
Clients, please reach out to your Account Manager, or connect with us at info@systemsengineering.com or call 888.624.6737.