The prevalence of video conferencing is changing the way we conduct business. As we adapt to this new meeting practice, cybercriminals are adapting as well. The recent surge in use of cloud-based video conferencing technologies creates opportunities for cybercriminals to reengineer their phishing tactics.
We all are becoming accustomed to many requests for authentication throughout the workday. This reality appears to be how hackers are targeting individual users. In the last week, one security research group uncovered a couple of notable phishing attacks. These scams targeted end-users, rather than the security vulnerabilities within the platforms. Both attacks had four identifiable steps designed to fool unsuspecting users, with the end goal to steal their login credentials. Understanding the latest phishing scams can help you better protect your business. Take a look at the anatomy of these new clever attacks.
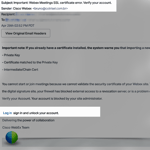
1. Impersonating Automated Emails
Generally, the impersonal nature of automated emails is not suspicious. End-users are familiar with application updates or password reset prompts. Emails that appear to have authentic product branding would not raise a red flag. It would not be unusual for the recipient to follow the recommended actions. This is how the hackers initiated the latest phishing attempts. By using exact replicas of existing system notifications. To the untrained eye, it makes detection almost impossible for the recipient.
2. Creating Urgency
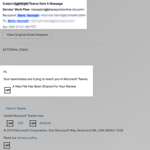
Another commonality between the two attacks was the urgency in the requests. One email notification was a common request for the user to install a system update to gain access to a virtual meeting. The other email spoofed a collaboration system notification by indicating that coworkers were trying to reach out and needed a reply. Both emails were undetectable to the average user. By appealing to our sense of urgency, hackers expected that recipients would act in haste.
3. Hiding Fake URL Links
In both recent attacks, the request was to click a URL leading to a phony credential landing page. Hackers included the familiar product name within the URL to appear less suspicious. The URL was further hidden by inserting it within "linked text" in the email to disguise the fraudulent URL. Hackers set up these URL redirects to bypass detection of email protection services. The engineering of these attacks makes it very difficult for an end-user to recognize.
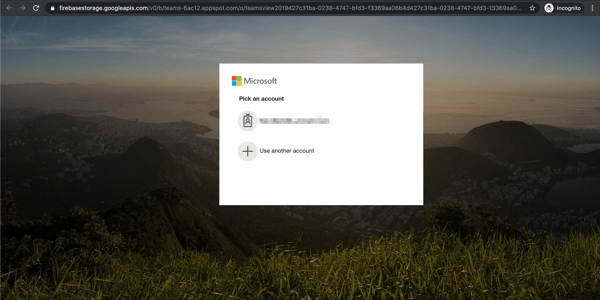
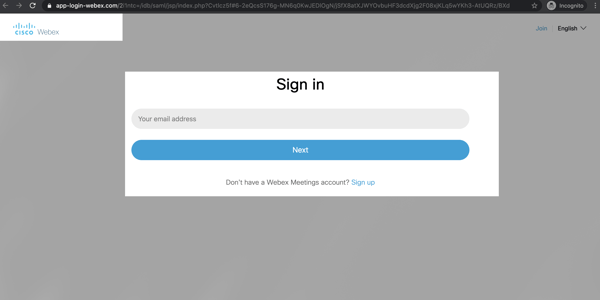
4. Stealing Login Credentials
The final step in these recent phishing attacks was to collect user login credentials. Cybercriminals impersonated the legitimate company branding and spoof authentic login pages. Since the imagery on the page is identical to the users' experience, it is hard to detect the attack. Under these circumstances, an unsuspecting end-user is likely to enter in their credentials, giving cybercriminals access to your business and its critical data.
Advice to Protect Against Phishing Email Scams
Creative attacks like these recent email phishing attacks reinforce why we need to be more vigilant than ever. If you or your employees receive a notification you were not expecting, you should delete or ignore it. This includes login prompts, via text, email, phone, etc. If it's a legitimate request, another notification prompt will go out again. Keep in mind, notifications will happen immediately after a login attempt.
Cybercriminals will continue to adapt and adjust to vulnerabilities presented during a change. And those vulnerabilities are not always in the software we use—it’s our employees too. It is our responsibility to stay informed and sensitive to this reality.
Would you like to learn more about educating your staff on the latest phishing tactics? Ask us about our Security Awareness Training. This program delivers interactive, on-demand security awareness training for your business. It reinforces proper end-user behavior through both annual education and on-going simulated phishing attacks to test your employees’ ability to spot and avoid phishing attempts.
Supporting articles from the security research group, Abnormal Security: