Your organization’s data is in the cloud, so now what? Is it secure? Where is it? Is it readily available? Who is accessing it?
At the most recent Systems Engineering (SE) Lunch & Learn, Artur Kuznetsov of Macpage and Jeff Trudel of SE discussed those very questions.

The event kicked off with an assumption that some businesses make about the cloud: My data is in the cloud, so therefore it’s compliant and secure. This assumption should never be made. Moving data to the cloud does not mean that the controls in place on the network servers in your office will be the same in the cloud.
And from an auditing perspective, assumptions are definitely not enough. Auditors require businesses to manage their own risk and to not assume risk is managed automatically.
Kuznetsov is the Manager of the Information Assurance Services team at Macpage where he advises clients in areas of IT and operational internal controls. He stated that he has seen many clients who assume that once their business’ data is in the cloud, security and compliance are no longer their concern. “While there are many benefits to the cloud including reduced costs, scalability, and flexibility, companies must remember that the overall responsibility of your data does not lie with the cloud vendor. Security and the ability to demonstrate compliance lies squarely with the company,” Kuznetsov confirmed.
As your company's data moves further into the cloud, it's important to understand the new security strategies available to protect your data. Trudel, SE Technology Consultant, followed Kuznetsov and gave attendees an overview on how the security perimeter has changed over the past few years.
Evolution of the Security Perimeter
Traditionally, companies used the castle-and-moat security strategy where a technology moat was dug to keep the bad guys out of using a drawbridge to allow trusted end-users into the network. The physical building itself was nice and secure, there was a firewall, an antivirus solution, a patching schedule, and so on. The Old Security Perimeter looked a lot like this:
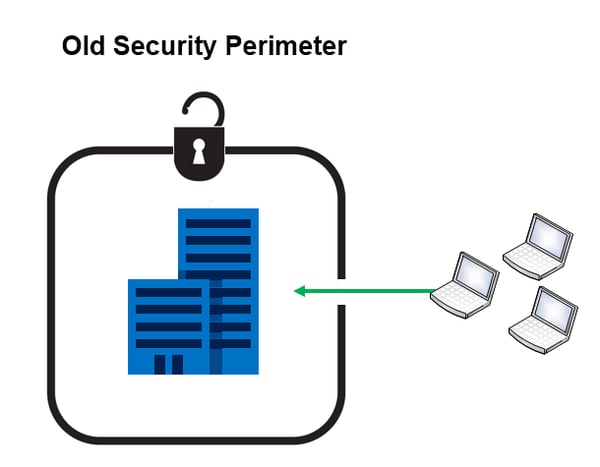
As businesses move data and processes to the cloud, our perimeters are growing and extending much further. Our data, once concentrated on internal servers, is beginning to be housed in different places, within many apps, accessed on a variety of device types. So now, we can no longer rely on the borders we relied on in the past, as much of our company’s data has gone beyond its four walls. 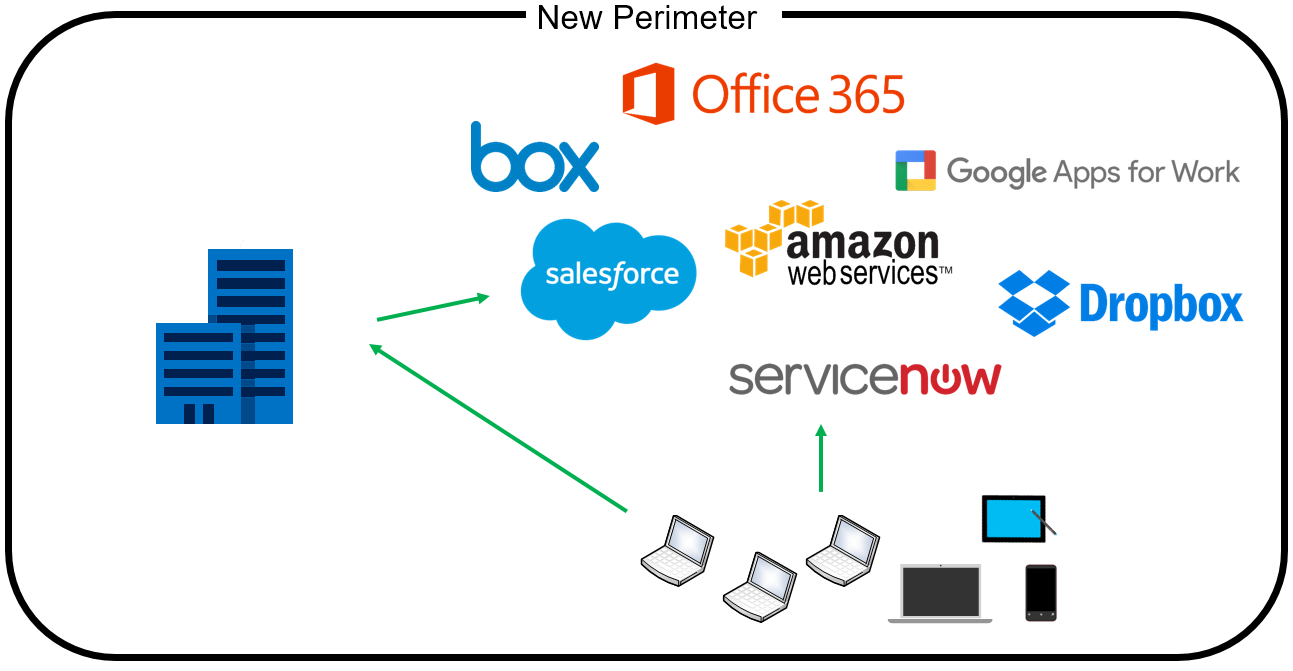
What should a small to medium-sized businesses (SMB) do to secure their sprawling security perimeter?
First, recognize your SMB will need to change the way it thinks about network security. If you or anyone in your company is using the cloud to do work, the old security perimeter (a.k.a. the castle-and-moat strategy) will likely be an ineffective cybersecurity strategy by itself.
Next, uncover the tools you currently have in place to understand how they could be effective in the new perimeter. Revising your cybersecurity strategy to include cloud doesn’t mean throwing out what you currently have. Much of your current technology will still play a future role in keeping your organization secure.
Wherever you are with your cybersecurity stance, don't let the expanding perimeter discourage you from the cloud. There are many powerful and flexible tools to help your small- or medium-sized business build or strengthen the new perimeter around its end-users, devices, apps, and data; all of which can be measured and monitored with auditing and compliance tools. Your best strategy is to not take this on yourself—work with a partner who understands how to build upon what you currently have to create a security strategy that works best for your business.
Modern Defense in Depth
To learn about the cybersecurity strategies and tools you can employ to protect your network, download the Modern Defense in Depth white paper.






