Every organization wants to stay off the cyber hacker’s radar, but with the increasing number of data breaches year over year, this is easier said than done. According to the latest report from the Identity Theft Resource Center (ITRC), the number of reported data breaches through Q3 of 2021 has already exceeded the total number of breaches reported in 2020 by 17%. So how can your organization keep from becoming part of the next statistic? A good place to start is to adopt the following patch management best practices within your organization.
Current State of Patch Management
Cybercriminals are actively scanning networks for unpatched, known security vulnerabilities, and having great success. A 2020 study conducted by the Ponemon Institute revealed that 42% of organizations surveyed said a data breach had occurred through an unpatched, known vulnerability. Even though patches were available, they were just never applied by the organization.
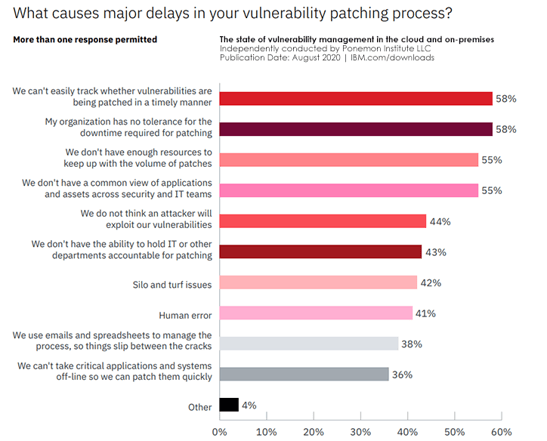
The study also uncovered the top reasons organizations have difficulty identifying and prioritizing their riskiest vulnerabilities (image below). The lack of a proper tracking mechanism and no tolerance for downtime topped the list. The trouble is, leaving even one unpatched vulnerability can lead to a major exploit. Organizations can address these challenges and mitigate the threat of a cyberattack by following patch management best practices.
Patch Management Best Practices
Every organization needs access to people, processes, and tools for effective patch management and network security. Here are a few best practices we follow internally to keep ourselves and our clients productive, secure, compliant, and up-to-date with newly discovered vulnerabilities and available security patches:
Identify a patch management team.
Create a dedicated patching team that focuses on proactive research of the latest bug fixes, security vulnerabilities, and feature update patches applicable to your network. This team should also maintain an accurate inventory of all the hardware and software elements connected to the network to ensure they are all cared for and none fall through the cracks.
Test patches before being deployed.
All available security patches should be tested for compatibility and reviewed for applicability or known issues. This ensures any given patch will not cause problems within your network, or assets to crash. This practice also helps determine which patches will be applied, delayed, or removed from that month's update.
Deal with patch exceptions.
When patches are identified that can't be deployed immediately or are excluded, a secondary review with a broader team should be completed. This team would look at how to limit risk for the asset exposed during the delay and assess what specific product or client needs may be discovered that justify keeping the patch in the update.
Automate patching where possible.
Apply the approved security patches to all affected endpoints using an automated vulnerability management tool and patching solution for direct and indirect cost savings to your organization. Automation directly reduces the time and effort of your patching team, and indirectly maintains a properly patched network and applications, reducing the likelihood of a breach and downtime.
Scan & report on exceptions and vulnerabilities.
Use your automated patching tool to identify any systems or endpoints that failed to properly update and then report out for patching compliance. It is also best practice to run monthly external vulnerability scans to identify any issues such as zero-day vulnerabilities that may require additional or immediate actions.
Overarching Best Practice
Avoid generational obsolescence.
An overarching best practice is to replace software once a manufacturer stops developing and servicing the software or operating system, better known as end-of-life (EOL). Once a product is EOL, the manufacturers no longer deliver technical support, upgrades, bug fixes, or security patching. Without these updates and patches, the aging technology becomes a greater risk to your organization. Hackers are on the lookout for these known vulnerabilities and count on exploiting them. Allowing generational obsolescence within your organization introduces a higher network security risk that can be avoided.
Security vulnerabilities, like unpatched networks and applications, bring significant risks and challenges for an IT department. You can mitigate these risks by adopting patch management best practices to stay up-to-date on the latest security patches and maintain the integrity of your network security program.
If your organization needs patch management support, visit our Endpoint Security service page. This service delivers critical security updates within your organization on a regular and timely basis.
Systems Engineering has security patching included with a number of our Managed IT service offerings. If you would like more information, connect with us at 888.624.6737 or info@systemsengineering.com. Clients, please reach out to your Account Manager.