The Department of Defense (DoD) officially published the final rule for the Cybersecurity Maturity Model Certification on October 15, 2024. CMMC compliance will start appearing in defense contracts as early as Q225 and be a requirement in all contracts by October 1, 2026.
CMMC is designed to ensure defense contractors and subcontractors adhere to information protection standards for federal contract information (FCI) and controlled unclassified information (CUI) mandated by federal regulation. The goal is to safeguard sensitive unclassified data at a level that matches the risk posed by cybersecurity threats, including advanced persistent threats.

The proposed rule revises aspects of the CMMC program to address public concerns, streamlining requirements for simplified compliance, prioritizing DoD information protection, and reinforcing collaboration between DoD and industry to address evolving cyber threats. A follow-on Defense Federal Acquisition Regulation Supplement (DFARS) rule is expected in 2024.
Here is a detailed list of what you need to know about the CMMC and the IT security hygiene your organization may need to address.
TABLE OF CONTENTS
-
What is the Cybersecurity Maturity Model Certification?
- Why did the DoD create CMMC?
-
Why is the CMMC framework important?
-
Who needs to comply with CMMC?
-
How to prepare for a CMMC assessment?
What is the Cybersecurity Maturity Model Certification (CMMC)?
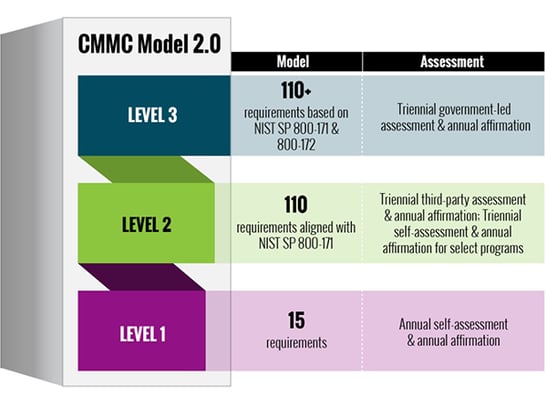
The CMMC 2.0 framework is organized into a three-tier model that requires companies entrusted with national security information to achieve a progressively advanced CMMC level, depending on where the Controlled Unclassified Information (CUI) or Federal Contract Information (FCI) to be protected is processed, stored, or transmitted. This protection also applies to information shared and exchanged with subcontractors in a multi-tier supply chain. The flow down of the CMMC requirements to subcontractors is necessary to respond to threats that reach even the lowest supply chain tiers.
Both CUI and FCI include information created, collected, or received, by or for the Government, that is not intended for public release. Specifically, CUI must also be safeguarded at every stage of existence (in use, storage, and transmission) until it is destroyed, disseminated, or decontrolled.
Certain DOD contractors that handle sensitive unclassified Department information will soon be required to achieve a particular CMMC level as a condition of contract award. Depending on the level (Foundational, Advanced, or Expert), an authorized and accredited CMMC 3rd Party Assessment Organization (C3PAO) will conduct a verification of the DIB company's cybersecurity posture and implementation of the required processes and practices. Upon completing the assessment, an independent CMMC Accreditation Body (AB) will award the DIB company the appropriate CMMC-level certification. The contractor's CMMC level is then stored in the Supplier Performance Risk System (SPRS). The DOD uses the SPRS to verify a contractor's certification level before awarding a contract, where required. The assessments are valid for three years and must be renewed every three years to remain current.
Why did the DoD create CMMC?
To best understand the CMMC Framework and Assessment methodology, it is helpful to know the origins of this rule. Protection of unclassified information through minimum cybersecurity standards within the DOD supply chain has been in effect on defense contracts since 2013. The regulations relied on the DIB contractors to self-attest that they will or have implemented the security requirements of the FAR 52.204-21 and DFARS 252.204-7012 clauses upon submission of a contract offer. These regulations fell short in the DOD's ability to assess and verify a contractor's compliance with the protection of government information before the contract was awarded.
The FAR clause mandates protection of any Federal Contract Information not intended for public release, provided by or generated for the Government.
The DFARS clause requires a DIB contractor to protect Controlled Unclassified Information in Nonfederal Systems and Organizations by implementing the up to 110 security controls under NIST SP 800-171 Rev. 2 DoD Assessment Methodology.
Why is the CMMC framework important?
Suspicion of non-compliance from defense contractors to implement the basic safeguarding and security requirements was realized when DIB contractors reported 248 security incidents to the DOD Cyber Crime Center between 2015 – 2018. These numbers got the attention of the Secretary of Defense, who subsequently requested an audit by the DOD Inspector General (IG) to determine whether contractors were protecting CUI on their networks and systems. The 2019 IG report findings indicated that DOD contractors did NOT consistently implement the mandated requirements. The report emphasized that "malicious actors can exploit the vulnerabilities of contractors' networks and systems and exfiltrate information related to some of the Nation's most valuable advanced defense technologies." The IG report recommended that the DOD take steps to allow for verification of a contractor's ability to protect CUI, which resulted in the CMMC Framework and Assessment Methodology.
Who needs to comply with CMMC?
The CMMC requirement applies to any company or group within the DIB sector that receives, handles, or processes FCI or CUI from the DOD. A DIB contractor that does not handle information deemed critical to national security (Level 1 and a subset of Level 2) will be required to perform an annual self-assessment, and a senior company official will need to submit an attestation form confirming compliance. These acknowledgments of compliance will likely need to be submitted to the SPRS as well.

Contractors that manage information critical to national security (a subset of Level 2) must align with the 110 security practices of NIST SP 800-171 Revision 3, and undergo third-party assessments from accredited C3PAOs. For the most critical defense programs requiring Level 3 certification, contractors will be accountable to a subset of the NIST SP 800-172 requirements, which are a supplement to NIST SP 800-171 Revision 3 and are currently under development. The DOD intends for Level 3 cybersecurity requirements to be assessed by government officials rather than accredited C3PAOs.
How to prepare for a CMMC assessment?
For many defense contractors and sub-contractors, preparing for a CMMC can feel like a daunting process. The good news is that Systems Engineering can get you there. We are a CMMC Registered Practioner Organization and have been working with the NIST SP 800-171 framework for years. We fully understand the cybersecurity processes and practices necessary to achieve CMMC compliance.
 If your organization needs to become CMMC Level 2 certified, we're here to help. We start with a CMMC Gap Analysis to identify missing or ineffective controls and practices in your environment. With this information, you can prioritize your gaps and create a plan for remediation.
If your organization needs to become CMMC Level 2 certified, we're here to help. We start with a CMMC Gap Analysis to identify missing or ineffective controls and practices in your environment. With this information, you can prioritize your gaps and create a plan for remediation.
If you have any questions on CMMC and how we can help prepare you for certification, visit our CMMC services hub, call us at 888.624.6737, or email us at info@systemsengineering.com.