The need for cyber risk management is growing exponentially. The threat of cybersecurity risks within small—to medium-sized businesses (SMBs) keeps many business leaders up at night. The business-wide disruption that a successful cyberattack brings and the increasing number of SMBs falling victim to cybercrime each year mean cyber risk can no longer solely be the responsibility of IT.
Business leaders are grappling with these new and unfamiliar risks. Leadership and IT must work together to manage and mitigate cybersecurity risks effectively. The fact is that cyberthreats are constantly evolving. Addressing cyber risks has become an ongoing process of analyzing, identifying, and evaluating evolving threats and implementing tactics and best practices to reduce the likelihood of and preparedness for a cyber crisis.
When interviewing candidates for a position on our Systems Engineering Advisory Services team, I almost always ask, "What is the right way to assess and manage cybersecurity risk?" Even the most seasoned cybersecurity professionals will pause to think about the best way to answer. The truth is...
There is no 'right way' to manage cybersecurity risks.
There are many moving parts involved when it comes to addressing cybersecurity risks. To break this process down, we have organized our recommendations into the following sections below.

1. WHERE TO BEGIN YOUR CYBER RISK STRATEGY JOURNEY
There is a lot of confusion around the topic of cybersecurity. When an organization begins the process of addressing and reducing risks and vulnerabilities, most decision-makers aren't even sure how to get started. If we were to ask 10 leaders what they believe is the right way to do a cybersecurity risk assessment, we'd get 11 different answers. The response is often a version of, “I'm not sure where to start” or jumping directly to the logistics of what to do.
Here is a simplified outline of the steps it takes to address and reduce cybersecurity risks. Each step will be outlined in greater detail below.
-
-
Assess & communicate risks
-
Put risk decision-making where it belongs (within the organization)
-
Make informed decisions
-
Reevaluate risk (do it again)
-
2. ORGANIZATIONAL PERSPECTIVE ON CYBERSECURITY RISK
“It won’t happen to my organization.”
The confusion around cybersecurity stems from an organization's perception of risk, or better stated, misperception of risk. This is especially true for a small- to medium-sized business (SMB) that has NOT been hit by a cyberattack or has no first-hand knowledge of a company that has. It is not that companies today are unaware of the risks in play; it is the perceived likelihood of the event happening to them, leading to inaction or complacency. When referring back to our previous blog, Ways to Approach and Measure Your Cybersecurity Risks, we looked at how to calculate risk:
Risk = Likelihood x Impact
We see that minimizing the likelihood of an event happening will have a great impact on how that risk is perceived.
Once an organization has the displeasure of experiencing a security event, its understanding and appreciation of likelihood and impact are greatly influenced. A quote by David Friedberg, a Silicon Valley entrepreneur, gives us insight into risk. He states that data is the key to reducing the problem of perceptions influencing our risk equation.
“What is risk? Risk is uncertainty about the outcome. The less data you have, the more uncertainty you have about the outcome.”
– David Friedberg
When you gain a better understanding of actual risk, in essence, you have the ‘data’ needed to make informed decisions. This is a much better practice than relying on gut feelings or misperceptions of risk. So what is important to understand about cybersecurity risks? There are three key questions to ask:
3. CHALLENGES TO CYBER RISK ASSESSMENT
When it comes to assessing and understanding risk, there are many challenges to overcome. The biggest hurdle for most SMBs is where to start.
Picking a security framework
There are many frameworks to choose from depending on your industry (e.g. NIST Framework, CMMC, SOC 1 or 2, HIPAA, PCI, CIS, HITRUST, FFIEC), and all of them are about 80% the same. These are very good starting points for sector-specific guidance, understanding the set of controls you should deploy (what am I doing, what am I not doing), and focus on industry compliance. Unfortunately, what these frameworks cannot possibly do is cover all the cybersecurity risks that need to be managed.
It is challenging to follow what compliance factors your organization needs to meet and how to relate them to your environment. Once identified, highly specialized skill sets are needed to login to your network or cloud environment to run scans, review configurations and system design, and then subsequently interpret the results in a meaningful way.
Successfully communicate risk
Once risks are identified, it can be hard to understand what the cybersecurity impact is on an organization. Internal IT can have a hard time conveying the business impact of risk when asking for budget and resources from leadership. And conversely, it can be difficult for leadership to make budget decisions without fully appreciating the cybersecurity impact on risk.
4. CHALLENGES OF CYBER RISK COMMUNICATION
When looking at an organization and how it relates to risk, the area of responsibility can be grouped laterally. At the beginning of the line is the technology. This is everything that makes up a network, such as laptops, applications, firewalls, cloud, etc. Next, are the people that interact with this technology, such as clients, employees, and administrators, who follow procedures to help them interact with the technology. These two areas are where cybersecurity threats and vulnerabilities lie.
Cybersecurity Risk Decision Making
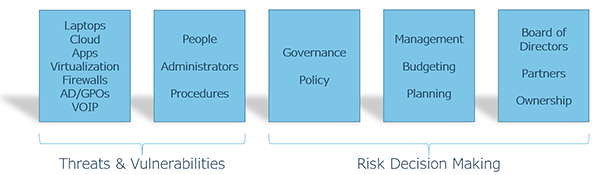
Moving further away from technology we find governance and policy. These are the frameworks that an organization has adopted to place guardrails on what we do and don’t do with technology, data, people, and process. Next in line is management, leadership, budgeting, and planning. In recent years, cybersecurity risk decision-making has expanded to an organization's board of directors and ownership. This was not the case a couple of years ago, which highlights the evolving level of concern for managing cybersecurity risk among business leaders. When it comes to cybersecurity risk management, these are the areas that all the risk decision-making happens.
The challenge with this arrangement is that attackers are trying to infiltrate and exploit the systems and staff in a completely different area than where the cybersecurity decisions are being made. This visualization demonstrates the need to communicate a great deal of information on threats and vulnerabilities to the decision-makers within an organization, and where the risk decision-making belongs.
It should not be left with IT alone to decide the acceptable level of risk for your organization.
5. RISKS TO CYBER RISK MANAGEMENT
We have already looked at the challenge of knowing where to start with risk management, and now we need to look closer at the issue of inaction (or complacency) due to the misperception of risk. Many times, this can be due to assumptions and misinformation coming from a company's own IT staff. While this may be communicated with the best of intentions, it is no less a possible risk to an organization. Some of the assumptions we frequently hear from management are:
Just because it's getting done, is it being done well?
When handling an auditor, a company is not typically going to show auditors all their cards, asking auditors to log into their systems to judge the health of their back-end systems, nor do auditors typically possess the skillsets to do so. Companies are usually just trying to get through the audit unscathed.
As mentioned earlier, the third piece of key data needed to understand risk is to ask, “What am I not doing?”
Here are a few statements I have heard firsthand of misinformation given by IT when leadership asked the question, “How secure are we?”
This is not a good answer. This statement assumes that it is possible to be 100% secure, which is not attainable. There really isn’t even a finite set of questions that could be asked to completely cover security which would give a percentage score.
This is not exactly true. In nearly all cases when software or service is outsourced, you still have some responsibilities to ensure the integrity and security of your data. For instance, your Software-as-a-Service (SaaS) application provider surely can’t be responsible for knowing you have just terminated an employee and need their access revoked.
6. EXPECTATIONS OF A CYBER RISK ASSESSMENT
At Systems Engineering, we have put a lot of thinking and effort into how we talk about and consider risk. We’ve had many interactions with organizations directly after they became a victim of a cybersecurity incident. This experience, along with the thematic questions we answer for victim organizations, has helped us formulate what we believe should come out of a cybersecurity risk assessment.
It is always ideal to be proactive when it comes to risk rather than trying to recover after an incident occurs. Incident response plans are important to have in place.
We routinely do Cybersecurity Risk Assessments. Following are four critical topic areas we cover for you and specific the information you will gain to help better understand your risk.
Specifics on what needs to be done to minimize the chance of another cyberattack.
What areas of IT (e.g., cloud, applications) have no direct management assigned? These oversights create opportunities for neglect and subsequent risk.
Assignment of objectives and prioritizing of risk findings in a meaningful way. Often IT people will work to remediate the problem areas they are good at fixing or interested in, but that doesn’t necessarily mean those are the places you should start.
Ensure decision-making falls in the right area of an organization. Then take action on those decisions.
To be clear, a cybersecurity risk assessment is not an audit; it's an in-depth review of what is happening in your environment to highlight areas of concern. Take for example the area of server backups. An audit would ask the question: "Is a server backup in place?" - Check "Yes" or "No".
An assessment, on the other hand, would uncover answers to questions such as:
- Are backups being done properly?
- Who is supposed to be doing them?
- Is everything needing backup actually being backed up?
- Are server backups failing without sending an alert?
Questions like these are reviewed in over three dozen areas within a thorough cybersecurity risk assessment.
An assessment is not meant to replace or cover every single security framework, but the assessment should be derived from these frameworks, along with lessons learned from securing various environments. The value of conducting a cybersecurity risk assessment is in understanding where you are and what residual (remaining) risks might be.7. RESIDUAL RISK ASSESSMENT
We have already examined the challenges, risks, and expectations of cyber risk management. Now, we will review the idea of residual risk and how it relates to a cybersecurity risk assessment.
A good way to understand residual risk is to once again look at server backups. In the risk calculation of Risk = Likelihood x Impact, the event of server backup failure carries the risk of data loss and downtime.
Server Backup Failure Risk = Data Loss & Downtime
In most cases, the likelihood of data loss at the server level is high. This is evident from the high occurrences of ransomware, hardware failures, human error (deleting files), and insider threats.
Server Level Data Loss Likelihood = High
As for the impact of data loss, it’s not a stretch to assume that most of the data being backed up is sensitive and highly important to an organization, therefore, we have a high impact value.
Server Level Data Loss Impact = High
So, when considering this data loss risk scenario for a server-level backup failure, we have:
high likelihood x high impact = high risk.
Now let's factor in the process of nightly (or hourly, etc.) server backups you'd likely have in place. This action of a backup routine is the control you have deployed to mitigate (minimize) the initial risk of data loss. This does not mean that the backups are being done properly, as we often discover in the vast majority of assessments performed. We typically find failing backup routines as well as overlooked systems that were never added to backup schedules long ago.
If we have a high initial risk and a poorly implemented control (backup routine), we have not removed much risk from the equation and are, therefore, left with a high residual risk.
Residual Risk = Risk – Control
The high risk of data loss, minus the backup control (being done poorly), still equals a high residual risk that needs to be addressed.
Ultimately, a cybersecurity risk assessment aims to inform an organization about its threats, vulnerabilities, and residual risks. Effectively managing cyber risks enables better risk management decisions and protects vital digital assets.
Many business leaders have been asking questions about cybersecurity, such as “Is our organization secure?” and “How secure are we?” Keeping your business secure is critical to its success, and we strongly recommend that every organization align itself to a security framework, such as NIST. Following a framework allows you to organize and prioritize cybersecurity risk reduction and create a multi-year improvement plan. Learn more about the business benefits of NIST here.
If you have any questions about addressing and reducing cybersecurity risks and vulnerabilities in your organization, please email us at info@systemsengineering.com. Clients, please reach out directly to your account manager.

Erik Thomas is Director, Advisory Services at Systems Engineering. Erik has over a decade of experience with IT, application development, and business operations. His group assists clients with the planning and implementation of IT systems, business development, cybersecurity risk assessments, and addressing regulatory compliance for businesses.