You may have recently received an email from Microsoft announcing the upcoming discontinuation of the Microsoft 365 Business Premium and Office 365 E1 “Grant” licensing, which is provided directly by Microsoft at no cost. Existing Microsoft 365 Business Premium and Office 365 grant recipients can continue service through their next renewal on or after July 1, 2025.
Mark Benton

Recent Posts
Microsoft to Discontinue Nonprofit Grant Licensing for M365 Business Premium and O365 E1
As organizations navigate the digital age, artificial intelligence (AI) will revolutionize various aspects of our work lives, including the way we work. In this post, we explore two types of AI experiences - Generative AI and Curated AI - and discuss which job roles can benefit from each.
As more companies embrace artificial intelligence (AI), the technology offers many benefits, including increased productivity and improved data-driven decision-making, among others. In fact, a survey from theSMB Groupfound that 53% of small and medium-sized business (SMB) respondents were “very interested” in the impact of AI on their business operations.
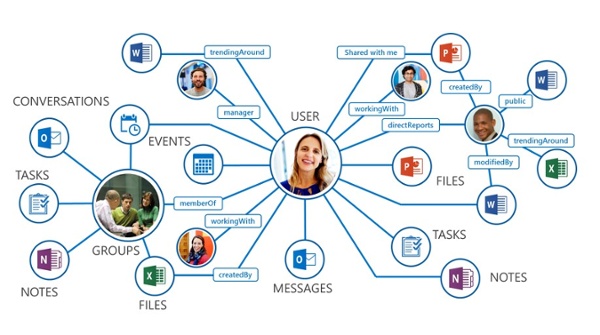
On Monday, January 15, 2024, Microsoft officially unveiled Copilot for Microsoft 365, extending its availability to all customers. Copilot for Microsoft 365 is a powerful set of tools that help to organize and connect your accounts, data, and online resources, but only for the data that users are allowed to see.
As a business leader, keeping your sensitive company data secure is a top priority. As your organization adds more security controls, access to applications may become more cumbersome. You and your staff are required to sign-in to multiple systems daily, each has its own set of credentials (usernames and passwords) and authentication methods. It's easy to lose track of credentials, and IT administrators are getting bogged down with password resets in addition to applying security policy enforcement within each of the various applications.
The AI landscape can be likened to the untamed frontier, marked by its rapid evolution, lack of regulation, and concerns surrounding data privacy and security. Despite the risks, the productivity and innovation potential have businesses across industries embracing AI. When ChatGPT was introduced in late 2022, it quickly gained traction, with over 100 million users adopting the platform within just two months, setting a new record for user growth.
OpenAI's ChatGPT is all over the news and creating a lot of questions. The goal of this blog is to help clarify what this all means, where it's headed, and what precautions you might want to take as an organization responsible for protecting sensitive and personal data.


.png)