As a business leader, keeping your sensitive company data secure is a top priority. As your organization adds more security controls, access to applications may become more cumbersome. You and your staff are required to sign-in to multiple systems daily, each has its own set of credentials (usernames and passwords) and authentication methods. It's easy to lose track of credentials, and IT administrators are getting bogged down with password resets in addition to applying security policy enforcement within each of the various applications.
Security is a paramount concern, and effective security measures should be implemented, but not to the point it impacts your staff's productivity and increases frustration. Numerous credential challenges can be solved by implementing a Single Sign-On (SSO) solution. With SSO, you bolster information security while maintaining end-user productivity. Your employees no longer need to remember numerous usernames and passwords for each enterprise application, and your IT admins stay focused on more strategic support tasks.
How Single Sign-On Works
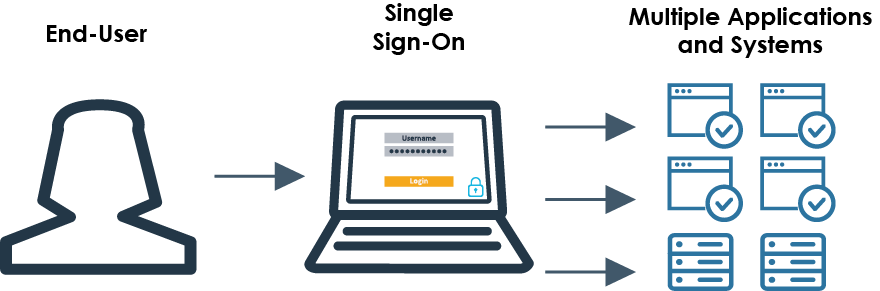
Simply stated, Single Sign-On allows a user to login on an SSO home-page that grants access to multiple enterprise applications and systems. Once the user's credentials are validated, the SSO system grants access to other trusted/configured enterprise applications. SSO can be viewed as a virtual traffic cop between end-users, endpoints, and applications they use. When a user wants to login to a particular application, the SSO system provides their valid credentials on their behalf. This process provides the end-user with a seamless experience when accessing configured systems and applications. In the case of a cloud-based SSO solution such as Azure AD, thousands of third-party SaaS apps are already pre-configured, saving IT administrators significant time in getting their users and cloud apps under control. Some of the administrative features allow for global security policy enforcement, assignment, revocation of access to certain apps, and password strength monitoring.
There are different types of SSO implementations, and the setup depends on what kind of integration your company requires. Is your company running cloud applications, or have a hybrid of on-premises legacy applications and modern cloud resources? Either way, there is a single sign-on experience available for convenient and secure access to your apps and critical data.
Benefits of Single Sign-On
-
Decrease time and frustration for end-users signing into multiple applications.
As more apps move to the cloud, that means separate usernames and passwords for each. It is not uncommon to switch between multiple applications or systems every hour, so having just one login to deal with improves overall usability and employee satisfaction. -
Minimize the number of help desk tickets submitted for forgotten passwords. Every application generally has a different set of credentials. If an end-user forgets their password, a password reset through IT may be required. This can mean downtime for end-users and unnecessary tickets generated for Help Desk. Using SSO eliminates the need for multiple passwords, and most SSO solutions give users the ability to reset their own passwords without IT involvement.
- Improved security with reduced need to handle and remember numerous login credentials.
A security best practice uses a unique, complex password for each application, but statistics show that over half of end-users will reuse passwords across business and personal applications. This is a security problem for not only cybercriminal activity, but also regulatory compliance. By having one set of secure credentials, the organization's attack surface is greatly reduced.
- Lower IT administration costs for user addition and removal, as well as user access level management.
Each application and system will require provisioning of policies based on user role, location, and other user traits. Typically, this process must be done separately for each. Since SSO uses a central authentication point to manage users, this enables a faster, less expensive process. Most importantly, it gives you one central place to remove user access to critical apps and data.
SSO and MFA: A Powerful Cloud Security Combination
One of SSO's best complements is Multi-Factor Authentication (MFA), and the two are not the same. As SSO enables seamless access to multiple applications and systems with one set of credentials, MFA authenticates the user and confirms their identity. As a matter of increasing security, MFA is generally required on a per-app basis. At Systems Engineering, we recommend enabling SSO in conjunction with MFA for applications or systems that hold a higher level of sensitive information.
As part of a larger cloud security strategy, Single Sign-On is an important element that safeguards your business against cybercriminals. It not only bolsters your security posture, it allows your staff to remember only one set of credentials to login to multiple systems and apps. SSO significantly simplifies the login experience for staff which they will thank you for.
If you would like to learn how SSO fits within your cloud security strategy, contact us at info@systemsengineering.com or call 888.624.6737 to speak to a Systems Engineering representative. Clients, please reach out to your Account Manager.
 Mark Benton is the Director of Product Management at Systems Engineering. He has over 30 years of experience in Information Technology and is responsible for overseeing the onboarding of new products and services for Systems Engineering and its customers.
Mark Benton is the Director of Product Management at Systems Engineering. He has over 30 years of experience in Information Technology and is responsible for overseeing the onboarding of new products and services for Systems Engineering and its customers.