It can often seem like compliance requirements such as the Cybersecurity Maturity Model Certification (CMMC) are just another burden - a chore that pulls resources away from day-to-day business operations. It’s easy to lose sight of why these initiatives matter. However, the reality is that CMMC compliance is far more than
Should you immediately decide to select an enclave approach for CMMC? The real answer is that it depends. It’s an important strategic decision to make early on in your compliance journey. Understanding the pros and cons of the enclave approach—and the alternatives—will help inform which direction you choose. It comes down to balancing security with operational efficiency and productivity. Ideally, you are not giving up one for the other.
CMMC Compliance: How MSPs Can Help Prime Contractors Get Their Supply Chain Compliant
As deadlines for Cybersecurity Maturity Model Certification (CMMC) compliance draw closer, prime contractors face an increasing challenge: ensuring their own certification and supporting their entire supply chain in achieving compliance. This responsibility has become an urgent and complex priority for those managing defense contracts. The issue extends beyond the prime's readiness—subcontractors' compliance directly impacts your ability to deliver on the contract. The stakes are clear: one non-compliant subcontractor can jeopardize the entire supply chain.
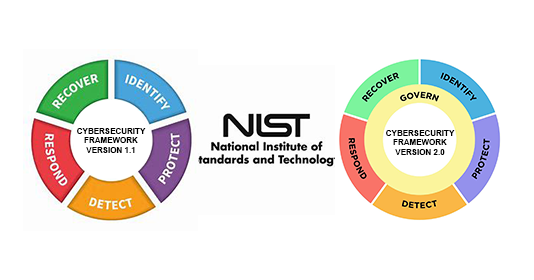
The newly updated NIST Cybersecurity Framework (CSF) 2.0 is here, and it’s packed with important updates that business leaders need to know to keep their companies safe. Let’s dive into what NIST CSF 2.0 means for you and why it’s more important than ever.
The Department of Defense (DoD) officially published the final rule for the Cybersecurity Maturity Model Certification on October 15, 2024. CMMC compliance will start appearing in defense contracts as early as Q225 and be a requirement in all contracts by October 1, 2026.
When considering a managed service provider (MSP) for your business, it's important to evaluate their approach to securing sensitive data. Conducting due diligence to ensure that the MSP has the necessary controls in place to protect your sensitive information is highly recommended.
In a recent presentation to business leaders, Kent Goodrow, a Systems Engineering client Account Manager, spoke about the evolution of identity and access management (IAM). He noted the increasing business exposure to modern threats due to work-from-anywhere, cloud-first environments. Kent detailed how IAM has evolved over the last few years and how it now works to protect access to corporate resources. Below is an outline of his presentation on implementing IAM as your organization's first line of defense.