Has it been a challenge to manage your complex environment due to the frequency of Microsoft 365 feature updates? Would you prefer less frequent updates since they can be unpredictable and disruptive to productivity? If this is the case at your organization, then we have good news for you. As of May 12, 2020, Microsoft announced the general availability of a new Monthly Enterprise Channel. Now, organizations can bring users the latest capabilities to stay productive and secure, but on a predictable, once-a-month release schedule.
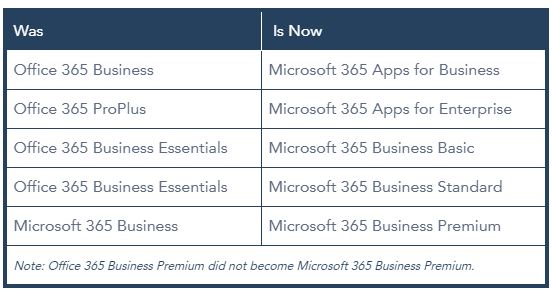
What’s in a name? As Juliet pointed out to Romeo, a rose could have any other name, and still smell just as sweet. This is essentially what Microsoft has done with their recent name changes to several of their Office 365 product suites. Going forward, all the product names of Office 365 for small to medium-sized businesses (SMBs) and Office ProPlus products will use the Microsoft 365 name, dropping the ‘Office’ brand.
Most businesses have some form of a wireless network (WiFi) in place, but is it really necessary to set up a separate guest wireless access? There are a few good reasons why this is an important step to take. We know having WiFi is imperative for employees who move throughout the office, but it also makes sense to offer wireless access to your guests, customers, vendors, and auditors. It's a cybersecurity best practice to set up a guest wireless network that is segregated from the corporate network, and here's why.
Many companies have made the unprecedented decision to close their doors or keep essential staff in-house temporarily. Others have instructed the entire organization to work-from-home (WFH) due to the COVID-19 pandemic. Now, an entirely new set of pressures is pulling for your attention:
Like many of you, we are working remotely as a company following the declaration of the COVID-19 national emergency. As previously stated, Systems Engineering is well prepared to continue working and supporting our customers during this time. As expected, the morning began with higher than usual support request volume. Many customers began their work from home experiences for the first time, and we were able to get them up and working along with our regularly scheduled services.
With the heightened awareness around the Coronavirus (COVID-19), we would like to share how Systems Engineering has prepared to handle potential upcoming challenges, as well as how you should be thinking through your approach. Over the years, we have worked with a number of our clients to develop Business Continuity Plans, applying critical thinking to how they would handle a pandemic scenario. These organizations are generally going to be better prepared to handle the uncertain path ahead.
When it comes to managing networks, businesses often fall victim to assumptions and oversights. The reality is that the protection of information and applications is always evolving and, as criminals find new ways to exploit weaknesses, it's tough to stay one step ahead.