Change is one thing we can all count on and the hardest thing to implement, especially when it comes to technology. Right now, the way we work has changed indefinitely, increasing our dependency on technology and intensifying cybersecurity risk. Hybrid work models and the rate of technology change make staying current with technology one of the most prominent challenges organizations face. Since productivity and security are two critical drivers of business success, not keeping up can put your business at risk.
As an IT managed service provider (MSP), we consistently see small- to medium-sized businesses (SMBs) targeted by threat actors. We can attest that companies following recommended security best practices have the tools in place to better prevent and respond to cyber threats. Now that our dependency on technology has quickly increased and cloud environments are becoming the new standard for productivity, the ability to securely manage and control access to your sensitive data and apps is a critical concern.
Some bad practices that are increasingly dangerous and raise the likelihood of a cyberattack can be taken directly from the Cybersecurity & Infrastructure Security Agency (CISA) playbook of exceptionally bad practices. Listed below are the current top three activities that increase your organization's cybersecurity risk and decrease your ability to attain proper organizational security and productivity:
1. BAD PRACTICE: Using single-factor authentication.
Allowing remote access to your company network using only one category of credentials (username and password) is known as single-factor authentication (SFA). Most commonly, password-based authentication is used with SFA, which relies on strong and complex combinations for security.
The main trouble with SFA is that users can be either unwilling or unaware of how to create and manage sufficient password combinations. This increases password-related calls to help-desk, and sometimes, policy changes that allow shorter, less-complex passwords. More frightening and a bigger threat to business security is end-users reusing passwords across multiple business and personal accounts, amplifying the risk of a breach.
SOLUTION: Enable Multi-Factor Authentication (MFA)
The most recent Verizon Data Breach Investigations Report stated 81% of hacking-related breaches are due to compromised, reused, or weak passwords. Multi-Factor Authentication, or MFA, has become a vital cybersecurity tool in preventing data breaches due to compromised credentials (username and password). It is proven to prevent some of the most common and successful cyberattacks. MFA supplements your password requirements, offering multiple layers of identity verification.
An example of MFA requires a device you hold, such as a smartphone or hardware token, to receive a one-time code, in addition to something you know, such as your login credentials. Learn more about MFA and how it protects your business and its critical data.
2. BAD PRACTICE: Using unsupported (or end-of-life)software.
When a manufacturer stops developing and servicing hardware or software, the technology has reached what is known as end-of-life (EOL). The product is dead in the manufacturer's eyes, and they will no longer deliver technical support, upgrades, bug fixes, or security patches. Without these updates and patches, aging technology becomes vulnerable to attacks and can compromise any systems connected to it. Continuing to operate on technology systems such as Windows 7, Server 2008, or Office 2010, which have been unsupported for a while, exposes your network to attacks and introduces a high-security risk.
Perhaps you are running critical EOL legacy applications or systems that have operated without incident for years, so the need to upgrade seems like an unnecessary investment. The fact is, the longer these EOL technologies are kept past their supported lifecycle, the more prone to failures the system will become, and the higher the cost will be to keep them running. At some point, that critical legacy application or system will stop communicating with modern technologies, and fewer people will be familiar with managing the product. This adds to your technical debt and creates potential productivity and operational risks.

SOLUTION: Upgrade to supported systems, stay current with patching, and control remote access to your network.
Upgrade to the latest supported technologies to reduce exposure to security threats, remain in compliance, and continue receiving the latest product upgrades and patches. We recommend planning for upgrades before they fall out of support to remain less vulnerable to security threats. You can accomplish this by automating the patching process through an endpoint security service to ensure your end-users and environment stays protected against security vulnerabilities no matter when they are discovered.
Another consideration in our cloud-connected, hybrid work model is the ability to control what mobile operating system versions are acceptable to access your corporate apps. The solution is Mobile Application Management (MAM) and provides encryption services and management features that allow for mobile access while retaining your organization's ability to control risk.
3. BAD PRACTICE: Use of default passwords and credentials.
Many software systems, appliances, web applications, and devices come from the manufacturer with default passwords already set up for administrative accounts. Often due to time constraints, the passwords will remain configured on an organization's internal network devices, significantly undermining security. This practice is used on networked devices such as IP phones and teleconferencing equipment, allowing for convenient access to maintenance services when needed.
When a new account is added to a network, the application may automatically add a predefined, auto-generated password, or if handled by internal IT staff, passwords may be assigned in a predictable way. It's common to have combinations such as:
- Organization Name/Address - (BizName123Main)
- Simple Creation Date - (Friday1022)
Of course, the first thing a hacker will look for is the use of the manufacturer's default credentials, which are publicly available on the internet. Also, the predictable and fixed password combinations can be easily compromised by cybercriminals who use hacking software, capable of cracking a 14-character, alphanumeric password in only 160 seconds. Once armed with the needed credentials, hackers can simply log in from the back end, and begin exfiltrating sensitive business information.
SOLUTION: Use SSO and SIEM solutions to manage multiple passwords and alert you to unusual network events.
Security is a paramount concern, and effective security measures should be implemented, but not to the point it impacts your staff's productivity and increases frustration. A solution like Single Sign-On (SSO) will take a single set of validated user credentials to grant access to other trusted/configured enterprise applications. SSO eliminates the need for employees to remember varying passwords across multiple configured systems and applications.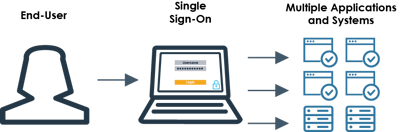
Your organization can also implement a Security Information and Event Management (SIEM) solution with the core function of threat detection and management, without over-burdening your existing IT resources. A SIEM solution can monitor and analyze your network, looking for deviations and potential security risks, immediately reporting on a harmful event. Once reported, a Security Operations Center (SOC) team can promptly respond to these detections and work to mitigate the impact on your business. By combining a SIEM solution together with a SOC team, any hacking attempts can be quickly recognized, identified, and rapidly remediated from the threat.
Keeping your business secure is critical to its success. Employing cybersecurity best practices, as suggested above, will go a long way in protecting your organization and its critical data.
"Is my business secure? How secure are we?"
These are two common questions we often hear from business leaders concerned about cybersecurity. When approached, our general recommendation is to assess your current business defenses. A quality Cybersecurity Risk Assessment will outline the cyber risks your organization faces, identify any gaps in defenses, and give guidance on how to improve your overall security posture.
For information about cybersecurity risks and how to improve your security posture, connect with us at info@systemsengineering.com or call 888.624.6737. Customers, please reach out to your Account Manager.






