The rate of technology change is accelerating, along with the number of attack surfaces within a company environment. At no time was the acceleration more evident than during the height of the pandemic. Many companies had to quickly adapt and invest in technology to simply keep operating. One study revealed that 60% of organizations introduced new cloud-based systems and tools to support a remote workforce and enhance their digital customer experience. This shift, however, also introduced new breach pathways.
To address the increased cyber threats, many businesses are conducting cybersecurity risk assessments to uncover weaknesses and gaps in their environment.
A cybersecurity risk assessment is a comprehensive review of your security defenses. It exposes vulnerabilities and determines if your organization has the right mix of security practices and measures to combat modern threats effectively.
Exposing any cybersecurity weakness within your environment is the essential reason to conduct a cybersecurity risk assessment.
The following is a list of other consequential reasons:
- CLARIFY YOUR CYBERSECURITY POSTURE
- ADAPT CYBERSECURITY STRATEGIES & PROTECTIONS
- PRIORITIZE CYBERSECURITY INVESTMENTS
- MEASURE CYBERSECURITY MATURITY & RESIDUAL RISK
- PREPARE AHEAD OF AUDITS
- EVALUATE EMPLOYEES' CYBER AWARENESS
- ANALYZE IT MANAGEMENT & GOVERNANCE
- OBTAIN/RENEW CYBER INSURANCE
- PROGRESS CYBER RESILIENCE
CLARIFY YOUR CYBERSECURITY POSTURE
As the saying goes, you don't know what you don't know. So what don't you know about your cybersecurity posture? Confusion around cybersecurity generally stems from an organization's perception of its risk or, better stated, misperception of risk.
Misperception is especially true for a business that has NOT been hit by a cyberattack or lacks first-hand knowledge of a company that has. A cybersecurity risk assessment clarifies your cybersecurity posture so you can evaluate and prioritize your risks.
ADAPT CYBERSECURITY STRATEGIES & PROTECTIONS

Beyond the pandemic, the rise of the cloud has changed the network topography for many organizations. As your network digitally expands, your cybersecurity strategy must evolve to defend against new cyber threats. A cybersecurity risk assessment will look across your network to evaluate what you are doing and, more importantly, what you are not. You can then create a cybersecurity roadmap and begin fortifying your cybersecurity defenses.
PRIORITIZE CYBERSECURITY INVESTMENTS
 Don't continue to waste your budget on cybersecurity protections that aren't effectively keeping out criminals. Not knowing how your defenses can be breached makes it difficult to know where to invest your cybersecurity dollars.
Don't continue to waste your budget on cybersecurity protections that aren't effectively keeping out criminals. Not knowing how your defenses can be breached makes it difficult to know where to invest your cybersecurity dollars.
Once a cybersecurity risk assessment is conducted, you should have a firm understanding of your level of risk (low, medium, high prioritization) for each area assessed. Risk is calculated by identifying a threat or vulnerability and evaluating the likelihood and impact of a compromise.
RISK = LIKELIHOOD x IMPACT
A cybersecurity risk assessment that applies this methodology will help your organization prioritize where to spend your defense dollars for greater effectiveness.
MEASURE CYBERSECURITY MATURITY & RESIDUAL RISK
Cybersecurity maturity estimates how effectively security controls have been implemented to help mitigate identified risks. A cybersecurity risk assessment should have context-aware interviews, documentation, configuration reviews, and automated scanning tools to help determine how well current controls are implemented and your level of residual risk. Generally, having a highly mature level of cybersecurity controls in place will help to reduce your overall cyber risk.
PREPARE AHEAD OF AUDITS
No organization wants to fail an audit; especially one focused on its defenses. In fact, cybersecurity risk assessments are now required by a growing number of regulations, standards, and laws. Before your next audit, conduct a cybersecurity risk assessment to identify where your security controls are ineffective or nonexistent. This valuable information can help you stay on top of cybersecurity and meet your compliance obligations.

EVALUATE EMPLOYEES' CYBER AWARENESS
Cybersecurity is more than IT. The 2022 Verizon Data Breach Investigations Report states the human element was involved in 82% of 2021 reported breaches. This comes as no surprise - we are human, after all.
A cybersecurity risk assessment will give insight into the threats employees face so you can educate them on how to spot and address cyberattack attempts. While training employees is important, having technology in place, such as multi-factor authentication or identity and access management, can be a safety net thereby reducing your chances of a breach, should a human error occur.
ANALYZE IT MANAGEMENT & GOVERNANCE
Certain policies and plans are critical business continuity components your organization will rely on should an event or breach occur. A cybersecurity risk assessment will evaluate existing IT policies, IT planning, disaster recovery planning, and IT governance documents. A review of these documents and processes can uncover any weaknesses that introduce exploitable risks.
OBTAIN/RENEW CYBER INSURANCE
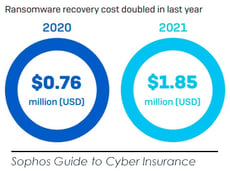
Cyberattacks and losses have increased over the past several years, leading to more demand for cyber insurance. Sophos Guide to Cyber Insurance states the average ransomware recovery cost for a mid-size organization hit $1.85 million last year, more than double the previous year's figure of $760,000.
The increase in losses has prompted insurance carriers to intensify cybersecurity requirements for businesses seeking coverage. Before you renew or obtain coverage, a cybersecurity risk assessment will uncover your systems' weak points. You can then address any vulnerabilities that may prevent your organization from obtaining cyber insurance.
PROGRESS CYBER RESILIENCE
Focusing efforts on cyber protection is a crucial exercise, however, proper attention must also be given to business recovery and continuation in the event of a cyber incident. The reality we face is that no organization is immune to a cyberattack, so addressing cyber resilience, which deals with recovery after an event, is equally important.
Conducting a cyber risk assessment will uncover weaknesses in your cyber defenses giving you the opportunity to address, mitigate, and build cyber resilience within your organization. By incorporating a cyber-resilient strategy your organization can limit the effects of a security incident while consistently delivering services, despite any failures resulting from an attack.
Cybersecurity is a never-ending race to outpace hackers. A cybersecurity risk assessment gives you a clear picture of your business's risk exposure. Knowing your organization's cybersecurity maturity and where weaknesses are in your defense posture can proactively address risks. Further preparing to respond and recover from a cyber incident will keep you a step ahead of the cybercriminals.
Limit the effects of a security incident while consistently delivering services by becoming cyber resilient.
For more information on IT and security services, connect with us at info@systemsengineering.com or call 888.624.6737. Customers, please get in touch with your Systems Engineering Account Manager.